Cybersecurity in 2024: Stand against the new threats
Digitalization the biggest phenomenon in the world has shown that it holds a lot of benefits to establishments, innovation, and interaction. But it also led to the steady transformation of the more general types of cyber threats into their more developed forms. That is why as the world moves forward into the year 2024 it also comes with proof that hackers have shifted to the use of technology to assail individuals, organizations, and even countries. That is why it can be implied that if the threats are in some way different, so are the ways of eliminating them. According to what was said throughout this article, it can be comprehended what main forms of cyber threats can be expected in 2024, and which approaches and tools are to be employed towards them.
The Evolving Threat Landscape: What’s at Stake?
As it has also been observed, the activity of cyber threats over the prior decade has significantly changed in a way with regard to the methods used. Today’s hackers are professional, rich, and inventive; hackers’ goals differ from monetary to reparative.
Ransomware 2.0: Beyond Encryption
 Although classical ransomware attacks are no longer new, the form of the ransom has evolved: encrypting ransom demands. The latest types of attacks involve taking data from the company and then demanding that the company pay the attacker a certain amount of money or the data would be uploaded on the Internet. This is how the so-called “double extortion” came to the forensics which puts the targeted businesses on the balance between the ruined financial loss and the equivalent level of reputational loss.
Although classical ransomware attacks are no longer new, the form of the ransom has evolved: encrypting ransom demands. The latest types of attacks involve taking data from the company and then demanding that the company pay the attacker a certain amount of money or the data would be uploaded on the Internet. This is how the so-called “double extortion” came to the forensics which puts the targeted businesses on the balance between the ruined financial loss and the equivalent level of reputational loss.
AI-Powered Cybercrime
Cybersecurity and cybercrime are two areas that whereby Artificial Intelligence utilized the most. This is the utilization of artificial intelligence to do the phishing, outsmart standard security systems, and create efficient and particularly individualized social engineering frauds. Today, these AI-incited attacks are total and quicker in scope, which has rendered them relatively difficult to trace.
The Expanding IoT Attack Surface
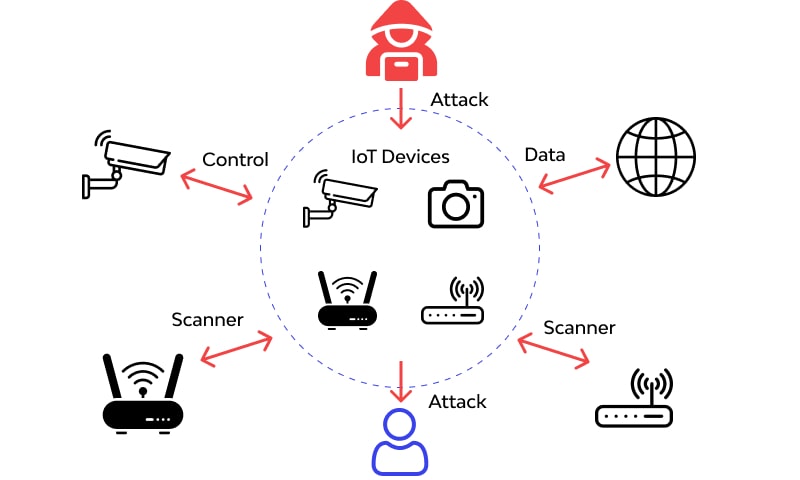 Of course, the introduction of the IoT has led to new risks such as risks associated with smart devices and industrial IoT structures. Devices and systems that are only somewhat successful can be used as a foothold by the attackers, and extend the scope of the attack to the rest of the network. With the advancement of IoT adoption, the risk is also increasing at a very high rate.
Of course, the introduction of the IoT has led to new risks such as risks associated with smart devices and industrial IoT structures. Devices and systems that are only somewhat successful can be used as a foothold by the attackers, and extend the scope of the attack to the rest of the network. With the advancement of IoT adoption, the risk is also increasing at a very high rate.
Supply Chain Breaches
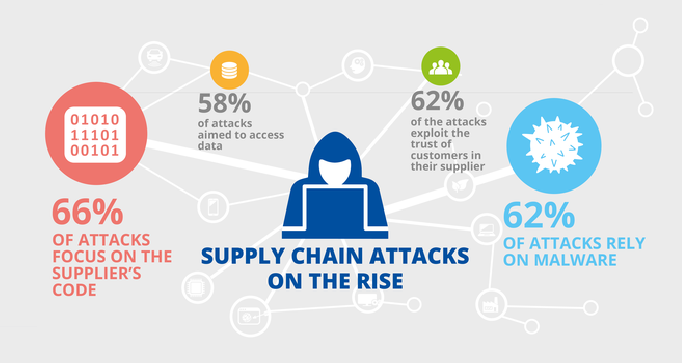 Every organization relies on its network of third-party partners and service suppliers, most of whom have inadequate cybersecurity solutions. These vulnerabilities are taken advantage of by cybercriminals to compromise the whole supply chain achieving large economic disruption.
Every organization relies on its network of third-party partners and service suppliers, most of whom have inadequate cybersecurity solutions. These vulnerabilities are taken advantage of by cybercriminals to compromise the whole supply chain achieving large economic disruption.
State-Sponsored and Hybrid Attacks
Cyber weapons are becoming the weapons of the choice being employed by nation-states for projecting geopolitical power. These complex, frequently stealth methods threaten strategic assets such as electrical utilities and healthcare or banking networks to unseat governments and erode confidence.
Fighting Back: How to Build a Resilient Cybersecurity Strategy
Cybersecurity is not an easy topic and it requires the use of technology, people, and processes when fighting cybercrime. Here’s how organizations can stay ahead in 2024:
Embracing Zero Trust Architecture
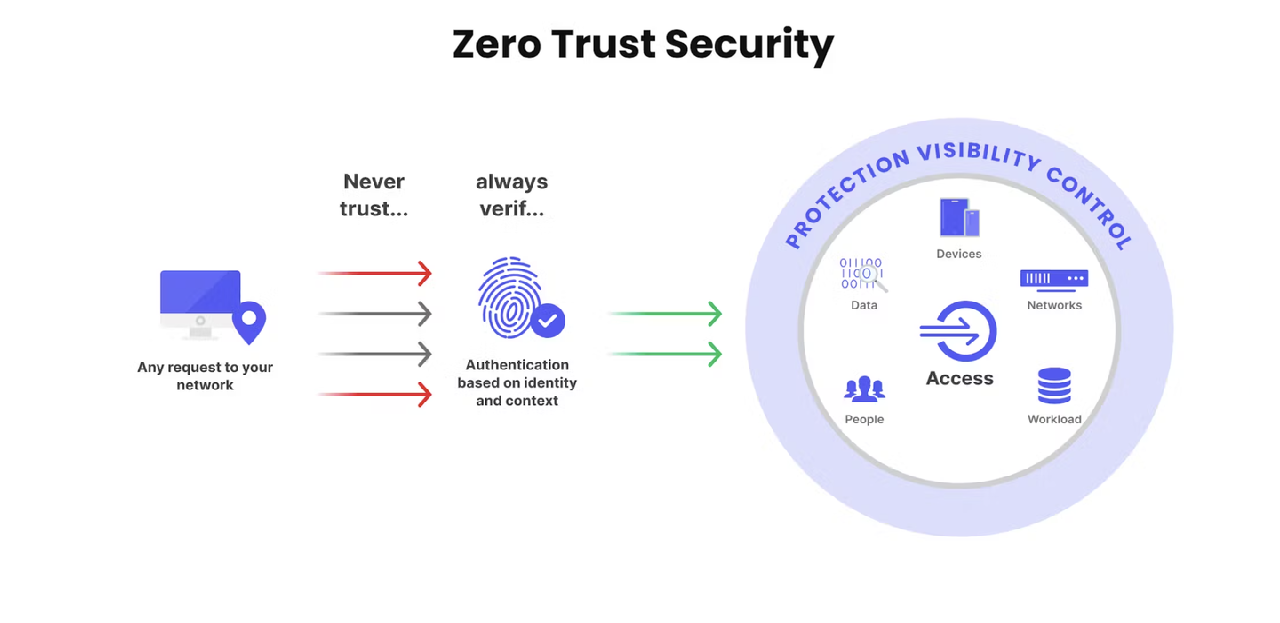 To state it simply, the only way to live in today’s world is to never trust and always verify. In Zero Trust Architecture, all users and devices must be validated every single time they seek to access the network and its resources hence limited penetration by malicious actors.
To state it simply, the only way to live in today’s world is to never trust and always verify. In Zero Trust Architecture, all users and devices must be validated every single time they seek to access the network and its resources hence limited penetration by malicious actors.
Leveraging AI-Driven Defense Mechanism
AI, or Machine Learning in particular, is not just a weapon in the hands of attackers, but rather a powerful weapon in the hands of defenders as well. Sophisticated AI technologies would pick up an anomaly, impending threat, and incident handling as well as a reaction to it in real-time, which remains beyond conventional cybersecurity approaches.
Strengthening Endpoint Detection and Response (EDR)
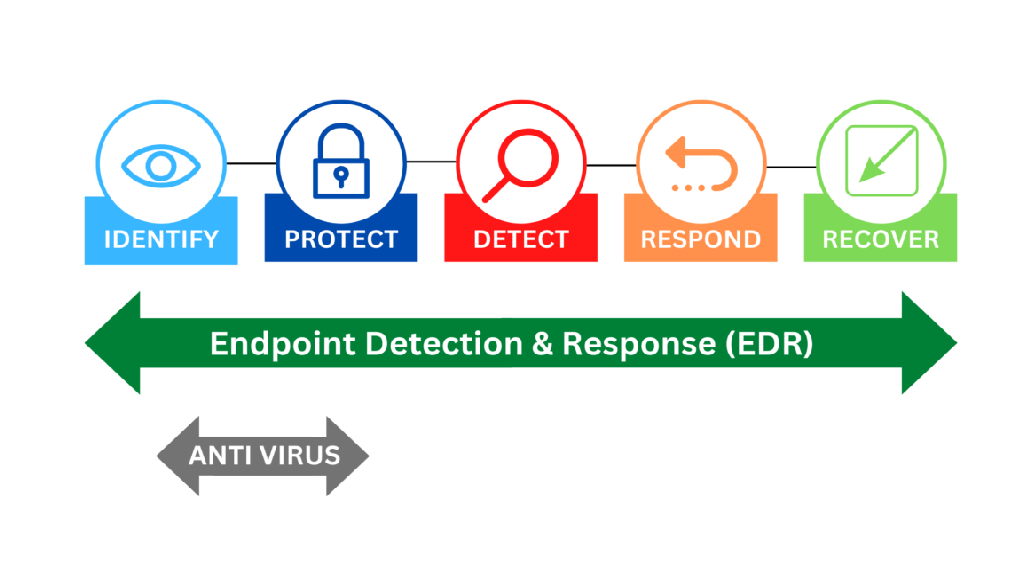 Since remote and hybrid work localized solutions are gaining traction, it is crucial to address the endpoint security issue. With EDR tools, the environment is continuously scanned, risks are identified quickly, and threats are resolved instantly on gadgets such as laptops, smartphones, and IoTs.
Since remote and hybrid work localized solutions are gaining traction, it is crucial to address the endpoint security issue. With EDR tools, the environment is continuously scanned, risks are identified quickly, and threats are resolved instantly on gadgets such as laptops, smartphones, and IoTs.
Regular Employee Training
As a result of a survey, the statistics revealed that the human factor is the primary reason for a successful cyberattack. Semi-monthly training sessions should enable the employees not only to identify phishing scams, protect their gadgets, and follow cybersecurity but also greatly minimize the risks.
Outsourcing to Managed Security Services (MSS)

Quite the opposite, for most other organizations it is a living nightmare to attempt to maintain an awareness of cyber threats. Working with MSSPs allows for the ability to leverage new technologies, excerpt monitoring, and compliance with the legal necessities which can stay with the organization’s key missions.
Why Proactive Cybersecurity is Important
Measures of the impact that are caused by cybercrime incidents are humongous and forecasted to amplify to over $10.5 trillion per year within the years to come around 2025. It also went on to produce a list on the likelihood of the loss of reputation, customer confidence, and national security at last. In such a context it is understandable that any operant that does not presume the existence of a reactive mode cannot again be acceptable. It is about time that business establishments and other institutions concerned should level up and at any one time search for another ‘new brilliant idea’ that a particular hacker has developed at that given point in time.
Conclusion
Now in 2024, it is more crucial than ever to learn more about cybersecurity. Due to the appearance of ransomware 2.0, attacks based on Artificial Intelligence, and supply chain risks, companies need to follow impenetrable and preventive approaches to protect their digital resources. The solutions are then in adopting concepts such as Zero Trust Architecture, AI in defense, and Quantum Key Distribution as well as constant training of the employees and contact with professionals in the field.
Cybersecurity is not a concept of avoiding a cyberattack; it is a concept of maintaining and strengthening organizational posture and reliability in the ever-expanding technological landscape. The risks are chilling, yet with proper strategies and allies, the fight against ever-growing forms of cyber threats can be conquered.
Cybersecurity is what drives the future. Threats should not be allowed to alter your vision. Contact Spark Technology today to do your part in creating a safer and smarter world online. Altogether as one society let’s guard the things we prize.
If you are looking for high quality web or app development services feel free to drop us a message

